data destruction
What is data destruction?
Data destruction is the process of destroying data stored on tapes, hard disks and other forms of electronic media so that it's completely unreadable and can't be accessed or used for unauthorized purposes.
When data is deleted, it's no longer readily accessible by the operating system, the application that created it or any other software tool capable of accessing data storage media. But deleting a file isn't enough; data destruction software must be used to overwrite the available space and blocks with random data until it's considered irretrievable.
Why is data destruction important?
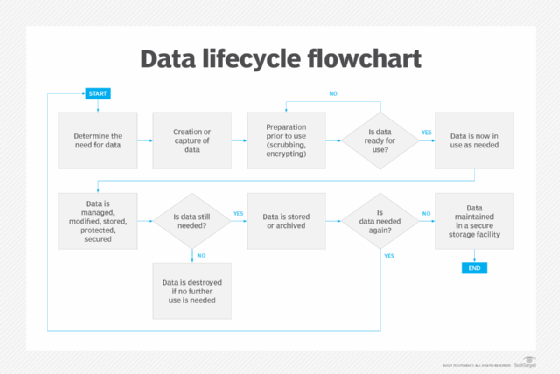
Data destruction is a critical security issue in data lifecycle management (DLM) and IT hardware lifecycle management.
Today's organizations must classify and store enormous volumes of data that are subject to data lifecycle management. Much of this data is business-sensitive, contains personally identifiable information or is otherwise affected by regulatory governance. Not only must data be stored and protected securely throughout its useful lifecycle, but it must also be properly destroyed when its lifecycle expires.
The data lifecycle can vary by data type. For example, customer data and product design data might have two dramatically different retention periods. Data lifecycle management policies, which are often designed around regulatory legislation and software tools, can help classify data and track its storage. These policies can also be used to alert business managers when specific data elements have reached the end of their retention cycle and are ready to be destroyed.
A close corollary to data lifecycle management is the concept of data privacy. In simple terms, data privacy enables the subjects of data collection, such as users or customers, to see, change and even request the removal of some data collected about them. In these cases, any data that's removed must also be destroyed and rendered inaccessible. The impact of data privacy on data destruction practices can be serious for regulatory environments, such as the California Consumer Privacy Act and General Data Protection Regulation.
Another corollary to data lifecycle management is the idea of legal discovery. All business data, from emails to product designs to user records, has potential evidentiary value in legal proceedings, such as a lawsuit. Discovery is a legal process by which evidence -- business data in this case -- is requested by the opposing party for the purpose of analysis and case development. The party subject to discovery must gather and provide the evidence requested.
Data that's properly destroyed in accordance with the organization's stated data retention policies generally isn't subject to discovery. However, data that's retained beyond its intended lifecycle or isn't properly destroyed at the conclusion of its intended lifecycle is subject to discovery. Consequently, proper data lifecycle management and data destruction can help to limit the amount of work needed by IT to meet discovery obligations if they arise.
Another consideration for data destruction is hardware repurposing. Aging IT gear is often recycled when it reaches the end of its working life or is supplanted by new gear through a technology refresh. The displaced gear, such as a storage subsystem, might be relegated to physical recycling, sold as used gear or reprovisioned within the enterprise for other uses.
Regardless of its fate, the displaced gear could still contain sensitive and protected data that must be properly destroyed before the gear leaves custody and control of the enterprise. Failing to destroy data prior to repurposing gear can carry the same implications and business penalties encountered by other types of data exposure or security incidents.
What are the different types of data destruction?
It's important to note that simply deleting data doesn't destroy it. Deletion is an abstract concept that simply marks the storage spaces used by the data as free rather than used. Those freed storage spaces can then be used by other applications and data at some point. Until then, however, the actual data in those storage spaces remains intact and can be recovered -- posing a potential security risk for the business. Data destruction means deliberately rendering the data inaccessible and unrecoverable.
There are two broad data destruction methods:
- Logical data destruction typically involves overwriting the data on the disk itself. For example, once data is deleted, another software tool overwrites the data content that remains present in those storage spaces. There are often several overwrite cycles to ensure that the underlying data is unrecoverable. The disk itself remains in perfect working condition and can readily continue normal service.
- Physical data destruction generally involves imposing physical mechanisms to erase magnetic data -- or even destroy the storage device entirely. Data can be destroyed through degaussing, which destroys data on magnetic storage tapes and disk drives by changing the magnetic field. One caveat with this method is that the person who wishes to destroy data needs to know the exact strength of degaussing needed for each tape type and drive. Degaussing is widely discouraged as a data destruction method. Degaussing works to erase the entire device -- where overwriting can target specific files -- so all the data on the device is basically destroyed. This can be effective when gear is repurposed. However, degaussing is ineffective with solid-state drive devices because there's no magnetic media to erase.
Storage media can also be physically destroyed by using a mechanical device called a shredder to physically mangle tape, optical media and hard disk drives. Of course, physically destroying a storage device removes that device from service permanently and reduces its business value to zero -- the business needs to buy new disks. However, destroying media can be a reasonable precaution for stringently regulated or highly guarded data.
What are best practices for data destruction?
There's no single formula to ensure proper data destruction. Every business is different and faces varied data sets and regulatory obligations. The most effective approach to data destruction is to craft practices that meet the unique needs and vulnerabilities of the specific organization, but such practices often include considerations such as the following:
- Understand the data. The first step in data lifecycle management is understanding the types and importance of the varied data types being stored by the business. Proper data classification techniques, coupled with well-considered storage tiering and data inventory tools, can help to track all data across the enterprise, ensure each data type is stored on a suitable tier for any point in its lifecycle and alert administrators for proper destruction when the data's lifecycle has expired. One of the worst vulnerabilities for any organization is orphaned data, which is stored and used but isn't properly tracked and managed.
- Understand the regulations. A business can be subject to numerous data protection and data privacy regulations depending on where it operates. It's important to recognize the regulations that pertain to the business and then craft data lifecycle and destruction practices that meet all those underlying obligations. For example, some regulations might impose longer data retention requirements on certain data types, while other regulations might not.
- Implement proper DLM. It's almost impossible for a single technology leader, or even an IT team, to manually track the lifecycle for every data element across an enterprise. The business must rely on suitable DLM software tools to inventory and manage all data; handle its proper storage, such as changing storage tiers over time; and, ultimately, schedule obsolete data for proper destruction.
- Select destruction methodologies. Understand what proper data destruction looks like. This might involve advanced data erasure, or overwriting, software tools, as well as the physical destruction of actual storage media. It's possible that different data types could require different destruction methodologies, so implement sound practices for each type. For example, if magnetic disks must be destroyed, sound practice might include placing such media inside locked storage while awaiting the scheduled arrival of a mobile data shredding service.
- Include third parties. Data protection, including data destruction, must extend to any third parties that access or possess the organization's data. Any contracts or agreements with third-party data processing or storage partners should absolutely include terms that define and enforce proper destruction of any business data in that partner's possession.
- Consider contingencies. Take the time to consider potential data storage and access contingencies and unexpected ways that data destruction could come into play. For example, if a storage subsystem is subject to a support contract and an outside technician must access the storage subsystem either remotely or in person, does data need to be migrated to other storage and destroyed from the afflicted subsystem before it can be serviced by an outside party? Similarly, if the storage subsystem is to be retired or repurposed, how should data destruction be handled for that subsystem to preserve data security and regulatory obligations?
- Ensure accountability. Regulatory compliance can require written validation or human confirmation that any data subject to destruction has been destroyed, whether logical destruction through overwriting or physical destruction through shredding. Policies should make provisions to include confirmation of data destruction by individuals responsible for managing that data. This could be as simple as a short form that simply details the data destroyed, who authorized the destruction, the method(s) used and the date accomplished. Such confirmations are typically part of the organization's overall data protection or DLM process.
Data destruction policies and standards
There are numerous standards currently available to provide data destruction guidance. Some of the most important standards include the following:
- ISO/IEC 27001. This broad, internationally accepted standard from the International Organization for Standardization (ISO) includes a systematic approach for managing and destroying sensitive information.
- NIST 800-88. The National Institute for Standards and Technology (NIST) 800-88 standard is perhaps the most widely used data destruction standard in the U.S. and covers disposal, cleaning, purging and destruction of various data media.
There are also numerous standards that focus on logical data destruction using overwriting tools, including the following:
- U.S. Air Force System Security Instruction 5020 (AFSSI-5020).
- U.S. Army Regulation 25-2 (AR 25-2).
- German Federal Office for Information Security (BSI-GS).
- Communications Security Establishment Canada IT Security Guidance 06 (CSEC ITSG-06).
- Russian State Technical Commission (GOST R-50739-95).
- British HMG Infosec Standard 5 (HMG IS5).
- Institute of Electrical and Electronics Engineers 2883 (IEEE 2883).
- U.S. Navy Staff Office Publication 5239 Module 26 (NAVSO P-5239-26).
- National Computer Security Center Technical Guidance 025 (NCSC-TG-025).
It's worth noting that most businesses aren't required to observe any specific data destruction standard as part of their own data destruction policy and practice. However, adopting or referencing an established data destruction standard can help the business craft a well-considered policy and can potentially help it defend against any data destruction errors or oversights when a broadly accepted data destruction standard is followed properly.
IT teams must take care when recycling mobile phones to safeguard data and prevent e-waste. Learn what sustainability methods organizations can use to ensure they aren't sacrificing data security or environmental sustainability.